

The promise of artificial intelligence in customer service was one of effortless support and unparalleled efficiency, yet the reality for many businesses has become a landscape of frustrated customers navigating clunky chatbots and overwhelmed agents wrestling with disjointed tools. This gap

The costly gap between a company's perceived service quality and the actual customer experience is often discovered far too late, typically within a churn report that signifies a relationship has already been lost. Most organizations are navigating their customer relationships using outdated

The relentless expansion of digital ecosystems has pushed traditional IT operational models to a breaking point, creating a chasm between business ambition and technical capability. For enterprises grappling with sprawling multi-cloud systems, aging legacy infrastructure, and complex microservice
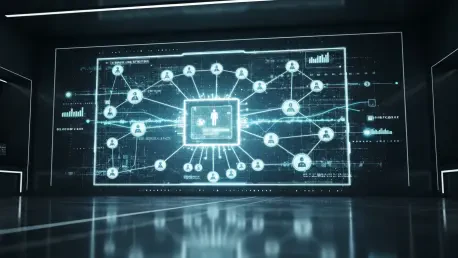
The silent hum of autonomous agents operating within corporate networks is rapidly becoming the new soundtrack of enterprise efficiency, yet it introduces a governance dilemma that few are prepared to solve. This emerging reality has catalyzed a strategic gold rush, with platform providers racing

As the wave of artificial intelligence integration continues to swell across industries, a significant number of organizations find themselves technologically unprepared to harness its full potential, creating a critical bottleneck for innovation. Industry data starkly illustrates this readiness
In a landmark move poised to reshape the continent's technological landscape, SAP announced the launch of its EU AI Cloud on December 17, 2025. This ambitious initiative is far more than a new product offering; it represents a direct and powerful response to Europe's urgent call for digital

With a remarkable talent for transforming vast datasets into compelling visual stories, Chloe Maraina stands at the forefront of Business Intelligence. Her expertise isn't just in data science; it's in her forward-thinking vision for data management and integration, helping organizations unlock the
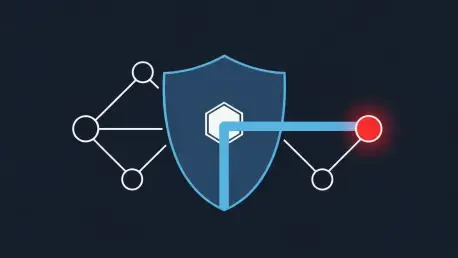
The initial signs of a major security breach are often indistinguishable from a routine operational hiccup, such as a sudden spike in CPU usage, an unusual pattern of network traffic, or a service that has become inexplicably slow. In many organizations, the IT operations team is the first to

The promise of artificial intelligence to revolutionize industries hinges on a resource that is simultaneously abundant and elusive: high-quality, analysis-ready data. While organizations are awash in information from countless sources, the vast majority of this data remains locked in disparate

In a landscape where the voracious data appetites of artificial intelligence applications are fundamentally reshaping enterprise infrastructure, the evolution of established open-source databases into AI-native platforms marks a critical turning point for the industry. The EDB Postgres AI platform
ITCurated uses cookies to personalize your experience on our website. By continuing to use this site, you agree to our Cookie Policy