

The humble office printer, often an afterthought in the age of cloud computing and sophisticated AI, has quietly become a significant gateway for costly cyberattacks and a bottleneck in organizational efficiency. This review assesses if intelligent print management technology is a worthwhile
In an industry bracing for a severe global memory chip shortage driven by the insatiable demands of artificial intelligence, Dell has made a decidedly counterintuitive move by launching its largest drive ever for the PowerStore platform. The introduction of a massive 30 TB QLC drive raises a

The silent, autonomous purchase of goods and services by artificial intelligence assistants on our behalf is rapidly moving from a futuristic concept to an imminent commercial reality, necessitating a common language for these transactions. The emergence of standards like Google's Universal
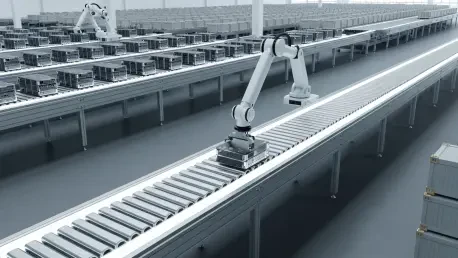
The modern supply chain, once a predictable sequence of linear events, now operates as a complex and volatile global network where a single disruption can trigger a cascade of costly delays. Into this high-stakes environment enters Artificial Intelligence, a technology poised to be the most

The thunderous race to train ever-larger artificial intelligence models has given way to a more pragmatic, yet equally transformative, challenge of deploying them efficiently at a global scale. This review explores the Vera Rubin AI Platform, a significant advancement in the enterprise IT sector

The hum of the server room, once the defining soundtrack of a Chief Information Officer's domain, has been decisively replaced by the complex and often cacophonous symphony of enterprise-wide strategic planning, cultural transformation, and relentless innovation. The modern technology leader stands

The romanticized image of a solitary creative genius wrestling with a blank page is rapidly becoming a relic of a bygone era, replaced by a dynamic dialogue between human artists and their intelligent digital collaborators. Generative artificial intelligence has moved beyond the realm of

In the rapidly expanding universe of large AI models, the insatiable demand for GPU computing power has created a profound paradox where scarcity coexists with immense waste. While these powerful processors have become strategic assets, their actual utilization rates often languish in the low
Beyond the pervasive headlines of revolutionary disruption and transformative potential, a much quieter and more practical application of Artificial Intelligence has taken firm root across the business landscape. Companies are increasingly turning away from costly, high-concept pilot programs and

The rapid advancement of large language models has undeniably transformed technology, yet a critical flaw persists at the core of their evaluation: a profound and limiting English-centric bias. Most systems designed to measure the capabilities of these sophisticated AI tools are built on
ITCurated uses cookies to personalize your experience on our website. By continuing to use this site, you agree to our Cookie Policy